Computer Network Sceurity and Informetion Tech
How to reset windows 10 Network security Computer Basic Knowloge Windows types network types and topologies CCNA Cicsco Vice Cicsco Sceuirty
Wednesday, June 24, 2020
Important Shortcut Keys System
Thursday, May 28, 2020
How to Install Kali Linux in USB Pen drive
1: Download
Kali Linux ISO Image from the official Kali Linux website
4: choose
the Bootable USB stick and you will see the Kali Linux installation option, In
that choose Live system
( 1st option ).
NOTE: While
entering to Live Kali Linux generally it won’t ask for username and password.
In case if it asked then Type “ root “
as username and “ toor “
as password.
5: Now open up your terminal and type the following commands one by one.
“ fdisk -l
#the above command will list out all the disk that are
available in your Laptop or PC . Now note down the USB name ( mostly it will be
/dev/sdb ).
fdisk /dev/sdb
#now it will ask you for command, type n and hit enter
Now press enter 4 times, and type w and hit enter.
#we have successfully created the partition.
fdisk -l
#now check whether the partition has been created or not
( copy the name of the partition that you created now eg: /dev/sdb3 )
mkfs.ext4 -L persistence /dev/sdb3
#wait until it complete and after it completes type,
e2label /dev/sdb3 persistence
#the above command will label the partition with the
name persistence.
mkdir -p /mnt/hackison (you can use any name )
mount /dev/sdb3 /mnt/hackison
echo “/ union” > /mnt/hackison/persistence.conf
umount /dev/sdb3
exit
#now reboot your laptop or Pc. and enter into your boot
menu
STEP
6: In the Kali Linux Boot Menu choose the 4th
option Live system (
Persistence )
STEP
7: Now Let’s check whether the persistence is working
good or not. To do that just change your background or create a new folder.
STEP 8: Now reboot your device and again enter into Live System ( Persistence)
NOTE: Each and every time when you want to go to persistence mode you need to choose that option.
Any qustions. hr610913@gmail.com
Monday, May 25, 2020
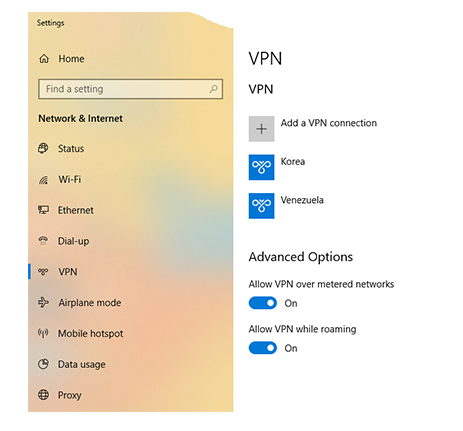
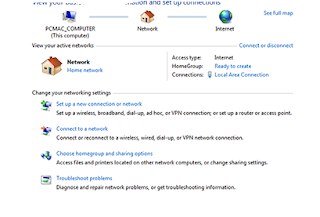
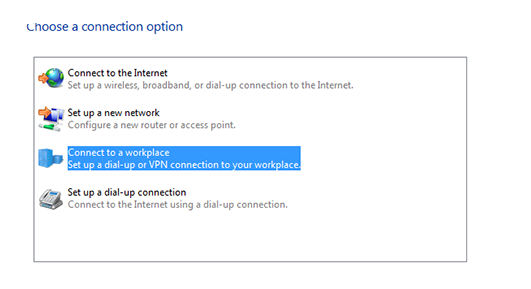
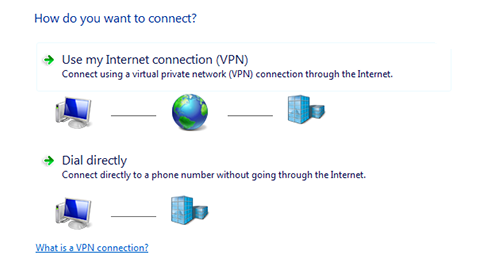
How to Configure VPN on Windows 10 Without any Softwaer
Configure VPN on Windows 10
In conclusion, Now you are ready to use Free VPN on Windows without any external software.
Enjoy using your Free VPN on Windows
If you have any suggestions regarding this article please mention in the comment section down below.
Smile (“_”).
Hostname Serch Thise Web site www.vpngate/net
pless see my post On Windows 7 VPN after see WIN 10
How to Setup free VPN In pc Windows 7 Without any Softwear
Setting up VPNGate Configuration
How to Manually add SCCP Phones to Cisco Communications Manager
Configure a SCCP phone and register the phone in Cisco Unified Communications Manager.
Activity Procedure
Complete these steps:
Before adding any SCCP phones manually into the CUCM, the MAC addresses of these Phones must be known. In this lab, for the SCCP Phones we will be using the VTGO phone. These phones will be added manually so the MAC addresses of these phones must be known/recorded.
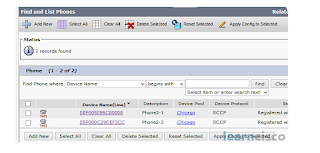
- On Cisco Unified Communications Manager Administration page, from the menu select Device > Phone.
- On Find and list phones, click Find button to list all IP Phones have been configured on the cluster. If this is a new installation, no IP phones will be listed.
- Click Add New button to add new IP Phone.
- On Add a new phone button, select Cisco 7965 for the phone type, and click Next.
- Select SCCP and click Next.
- Add phone with the following parameter:
- Device Name: MAC address which is used by this particular phone
- Description: Phone2-1
- Device Pool: Chicago
- Owner: Anonymous
- Phone button Template: Standard Cisco 7965 SCCP
- Device Security Profile: Cisco 7965 - Standard SCCP Non-Secure Profile - Click Save.
- On Phone configuration page, click Line [1] – Add a New DN link, to modify the phone number of the phone.
- Use the following parameter for the directory number configuration:
- Directory number: 3001 - Click Save and then Apply.
- If you want to add more phones, you have to repeat steps 3 – 10. For example Phone 2-2 will have the following configuration:
- Device Name: MAC address which is used by this particular phone
- Description: Phone 2-2
- Device Pool: Chicago
- Owner: Anonymous
- Phone button template: Default Cisco 7965 Template.
- Device security profile: Standard SCCP Profile for Cisco 7965
- Directory number: 3002 - Click Save and then Apply.
- Start the VTGO application for the required phones. (Site 2 Phone 1 & 2)
- Verify the TFTP Server configuration. It should point out to 10.1.1.10. You can check this by viewing the setting of the VTGO softphone.
- Now two IP Phones with number 3001 and 3002 have been added manually and calls can be made between these IP Phones using the 4 digit directory numbers.
Activity Verification
You have completed this task when you attain these results:
- The IP Phones are registered with Cisco Communications Manager, they are using the Device Pool for Chicago and the button template is assigned.
- A call between both IP Phones can be established.
IP Phone Registration
Task 1: Configure Communications Manager System Parameters
In this Task we will prepare Cisco Unified Communications Manager for IP Phones for 2 Sites. For Chicago (Site 2) the Branch Site we will manually add Phones.
Activity Procedure
Complete these steps:
- From Communications Manager Administration page, go to System > Cisco Unified CM Group.
- On the Find and List Unified CM Group page, click Find button to list all Communications Manager Groups that have been configured on the system. If this is a new installation, there will be one Communications Manager Group called Default.
- Click on Communications Manager Group Default to change its configuration.
- On Cisco Unified Communications Manager group configuration page, if this is a new installation by default only the publisher server is selected as member for the Cisco Unified Communications Manager group default. Since there is only one Communications Manager is this topology there will not be any servers listed in the available servers list.
- The first item on Selected Cisco Unified Communications Managers will become the active call processing engine for this Communications Manager group.
- Click Save button to save any changes on the system and click Ok to restart all active devices assign with this Communications Manager group.
- On the Cisco Unified Communications Manager Administration page, from the menu select System > Device Pool.
- On Find and list Device pools page, click Find button to list all device pools configured on the system.
- If this is a new installation, only one device pools called default is on the list.
- To add new device pool, click Add new button.
- Create a new device pool with the following parameters:
- Device Pool Name: Chicago
- Cisco Unified Communications Manager group: Default
- Date and time group: CMLocal
- Region: default
- SRST Reference: disable - Click Save to store the new device pools configuration
- Repeat step 10 – 12 for another device pools with the following parameters, but do not add a new device pool. Modify the existing device pool Default with the following parameters:
- Device Pool Name: SanJose
- Cisco Unified Communications Manager group: Default
- Date and time group: CMLocal
- Region: default
- SRST Reference: disable - Confirm that the cluster have two device pools - SanJose and Chicago.